Network Technology: Best Practices
The Cubro Visibility Fabric, including its industry-leading Network TAPs and Packet Brokers, provides essential foundations for compliance with Article 21 requirements.
Navigating the intricate challenges of network visibility and monitoring in 2024 becomes crucial for Communications Service Providers (CSPs) amidst the ever-evolving landscape of technological progress.
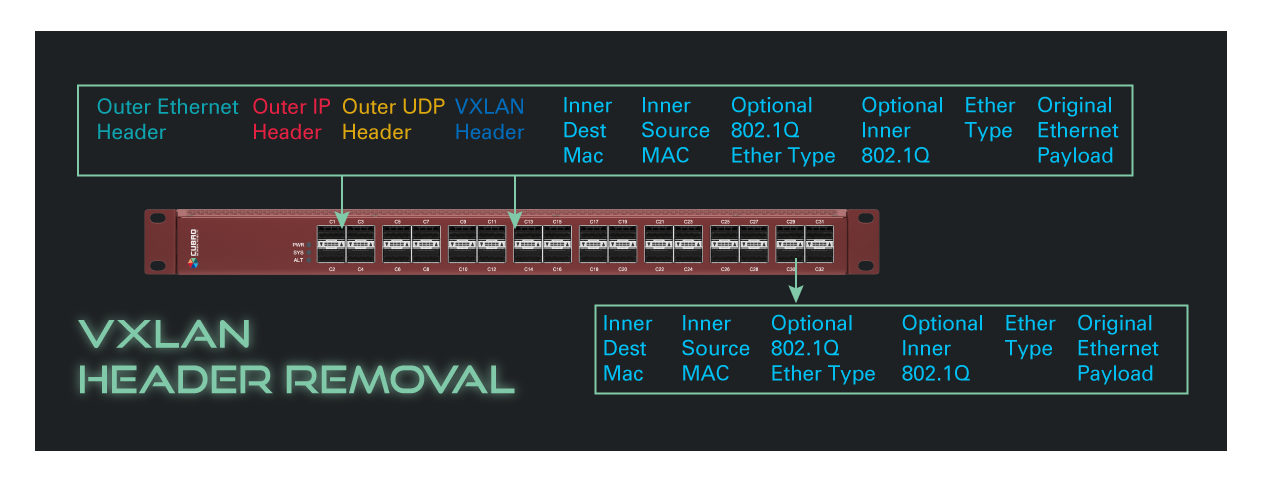
As MEC and distributed processing gain prominence, data transfer is streamlined with enhanced security. Cubro ensures GDPR compliance by addressing PII concerns in the data chain.
Discover how Cubro’s innovative solutions tackle the challenges of data explosion, optimizing network monitoring, security, and analytics while reducing costs and resource consumption.
As businesses continue to rely on technology for their operations, energy efficiency has become a top concern. Cubro has developed innovative ways to address this concern effectively.
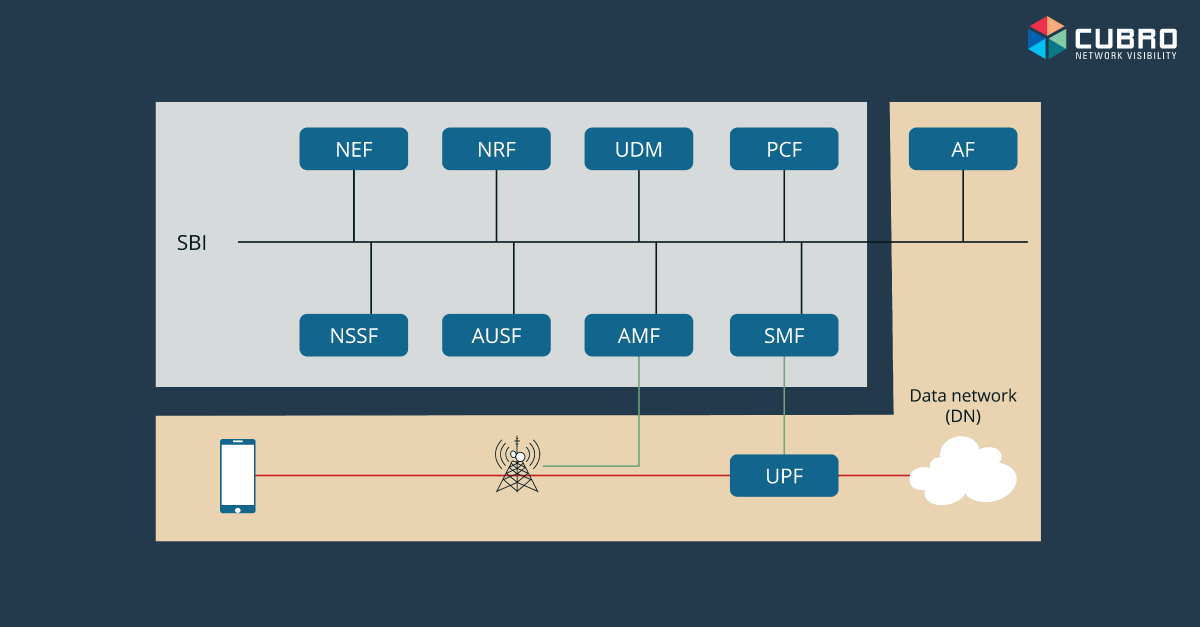
The importance of the 5G SA lies in the 5G promise of fully supporting enhanced mobile broadband (eMBB), ultra-reliable low-latency communications (URLLC) and massive IoT use cases.
In the USA, if someone tells you that you are “sassy”, it may be a nice complement… You are “bold and lively”. However, it can also be much less flattering, sometimes meaning: “rude and disrespectful”. You must listen carefully! For network managers, SASE, the Secure Access Service Edge, can be a great help, reducing infrastructure… Read More »What is SASE (Secure Access Service Edge)?
This blog focuses on the functionality comparison of network and security management. The frameworks aside, the Network and security operations teams have an ever-increasing amount of work and responsibility in taking care of the overall health, performance and security of a business.
Cubro Visibility products, together with Cubro security solution partners, can play a critical role in protecting enterprise computing access by continually monitoring network activity on the network to identify and remediate these new threats.
NPB technology can help businesses and organizations to significantly reduce the risk of not achieving or delaying a successful digital transformation outcome to help them increase their revenue, profitability and share value.
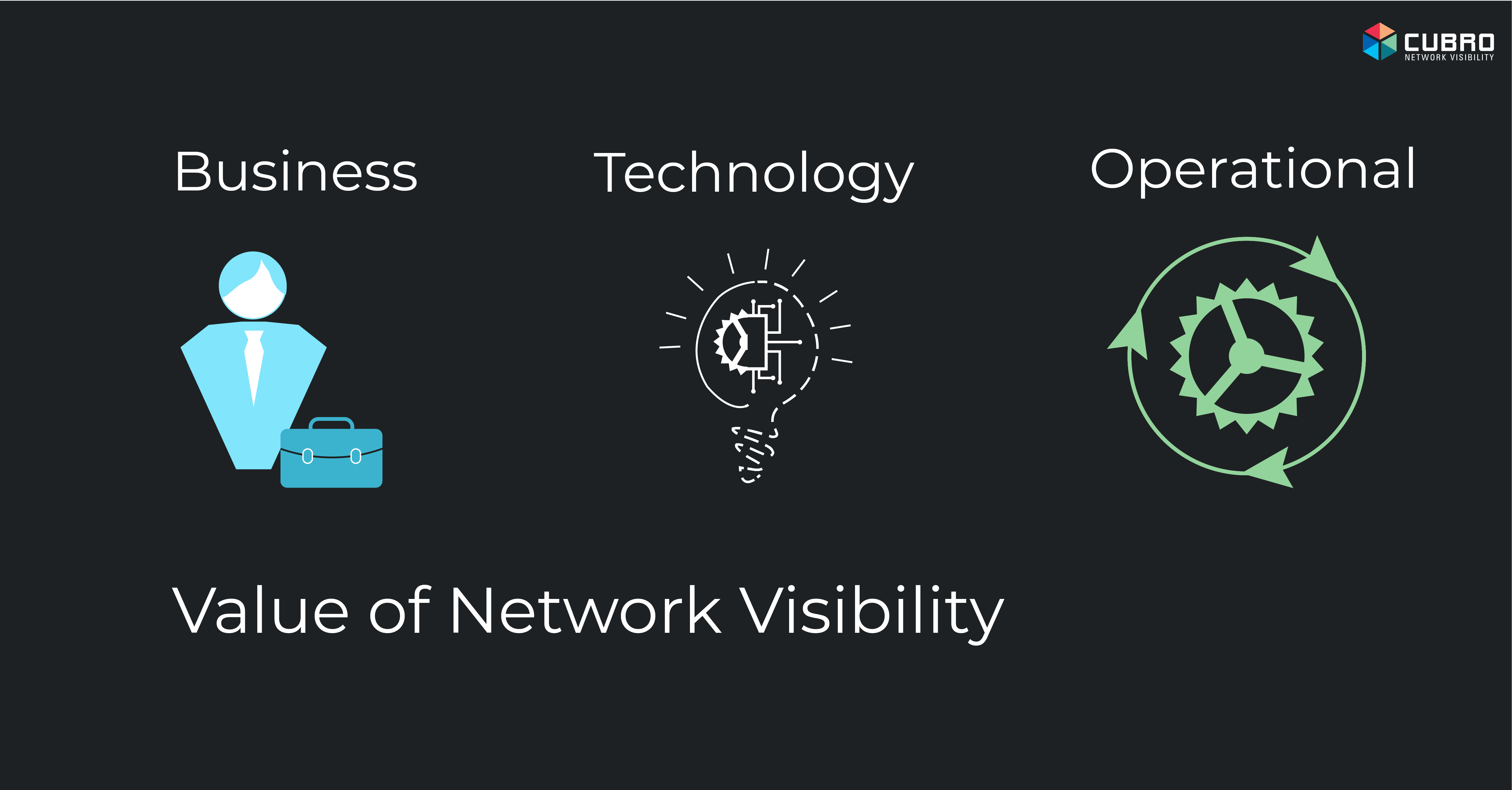
Network visibility technology has been deployed by Service Providers and Enterprises for the last 15 years or so and remains as important to a successful business and IT outcomes today as it was then. The use cases for visibility technology have developed as networks have changed and are now able to provide new, incremental value to organizations. The blog examines the value of visibility solutions and the reasons why they are essential for the success of contemporary IT initiatives and business outcomes.
Using Cubro EXA32100A, the customer can reduce business costs by making the team more productive. The service provider can save money because it needs to spend less on the cost of network operators.
Network requirements are constantly changing in enterprises. The network goal of every enterprise is to be more efficient and cost-effective while embracing the changes. There are several network visibility solutions/vendors available in the market …
In today’s digital landscape, enterprises and service providers rely on complex networks to manage vast amounts of data and ensure uninterrupted service. However, network outages and performance issues can have catastrophic consequences for businesses, leading to significant financial losses and operational setbacks. The Importance of Network Visibility to Prevent Downtime To minimize outages and performance… Read More »The True Cost of Network Downtime and Outages for Businesses
Getting the right network visibility architecture might be a daunting experience for the consumer because of the wide range of features, performance parameters, costs, etc which are part of the decision-making process …