In the USA, if someone tells you that you are “sassy”, it may be a nice complement… You are “bold and lively”. However, it can also be much less flattering, sometimes meaning: “rude and disrespectful”. You must listen carefully! For network managers, SASE, the Secure Access Service Edge, can be a great help, reducing infrastructure costs, enhancing security, end-user productivity, and IT efficiency. However, if it is not implemented carefully, it can cause much frustration to anyone dependent on a network to support their business operations.
The Secure Access Service Edge was coined by Gartner in 2019. According to Gartner, “SASE promises to overcome the limitations of too many tools and too many consoles. SASE combines common network functions with common security functions into a consolidated architecture with unified administration.”
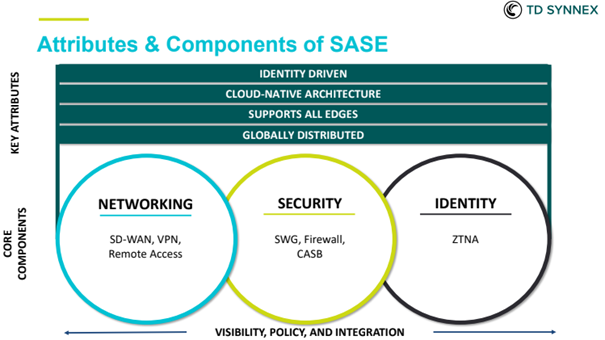
Gartner states, “The adoption of zero trust security architectures and branch office transformation projects — including software-defined WAN (SD-WAN), Multiprotocol Label Switching (MPLS) offload, internet-only branch — are accelerating the adoption of secure access service edge (SASE).”
The SASE architecture converges network (most notably, SD-WAN) and network security services (most notably Secure Web Gateway (SWG), Cloud Access Security Brokers (CASB), Zero Trust Network Architecture (ZTNA) and enables distributed policy enforcement to the enforcement “edge” that makes the most sense.
- The market for SASE implementation is expected to grow from USD$1.2B in 2021, to USD$4.1 billion in 2026 a 26.4% CAGR.
- By 2025, 50% of SD-WAN purchases will be part of a single vendor SASE offering, up from less than 10% in 2021
- By 2025, 65% of enterprises will have consolidated individual SASE components into one or two explicitly partnered SASE vendors, up from 15% in 2021.
The SASE architecture converges network (most notably, SD-WAN) and network security services (most notably Secure Web Gateway (SWG), Cloud Access Security Brokers (CASB), Zero Trust Network Architecture (ZTNA) and enables distributed policy enforcement to the enforcement “edge” that makes the most sense.
For many enterprises, with extensive branch networking requirements: retail, manufacturing, banking and finance, and healthcare to name a few, SD-WAN is often the first step on the SASE journey. SD-WAN implementations provide a network approach more in-line with today’s Internet-centric business models, offering compelling cost savings over traditional private networks.
While the policy and management of the SASE infrastructure is centrally administered and cloud-native, the policy enforcement is distributed and implemented where most effective. SASE functions such as SD-WAN, Secure Web Gateway and others are “in-line” network functions, which means, if out of service, they can become points-of- failure for business operations. If the device implementing the function needs to be taken off-line for maintenance, critical applications can be stopped.
This means that SASE implementation should be carefully planned, and include functions such as high-availability, load-balancing, and fail-safe capability. It is even more critical when multiple security functions are consolidated in a single device.
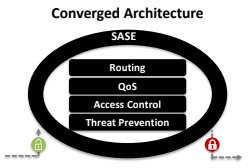
Cubro Bypass: Maintainability and Enhanced Availability for SASE Implementations
Cubro Bypass Switch is an essential tool for fail-safe, high-availability solutions that perform the task of ensuring uninterrupted service in the event of inline hardware failures. Cubro’s Bypass technology utilizes heartbeat packets generated and detected by the network interfaces to identify an interruption in the link, even when the failure is caused by a misconfiguration or a software fault. Cubro’s bypass switches uniquely include load-balancing functions in conjunction with the heartbeat-based high availability and failover capabilities that ensure any investment in enforcement tools is fully utilized.
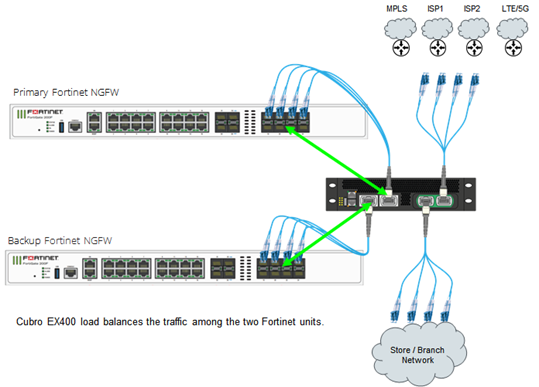
The figure below shows how a Fortigate SD-WAN implementation, including a variety of SASE functions, connects a large branch office or store to the corporate network, any cloud services, and its customers and partners.
Using the Cubro EX400 Bypass Switch, traffic is load-balanced across multiple converged appliances, providing enhanced availability and maintenance. Additional switching infrastructure is no longer required. Lower complexity means quicker implementation, faster time to benefits, and simplifies overall management of the solution.
Using Bypass switches to interface in-line network tools to enhance fault-tolerance and availability is a traditional approach to building resilient networks. Cubro’s industry-leading EX400 switch is a cost-effective solution that is built for today’s emerging network designs and security architectures.
