Network Technology Trends
As MEC and distributed processing gain prominence, data transfer is streamlined with enhanced security. Cubro ensures GDPR compliance by addressing PII concerns in the data chain.
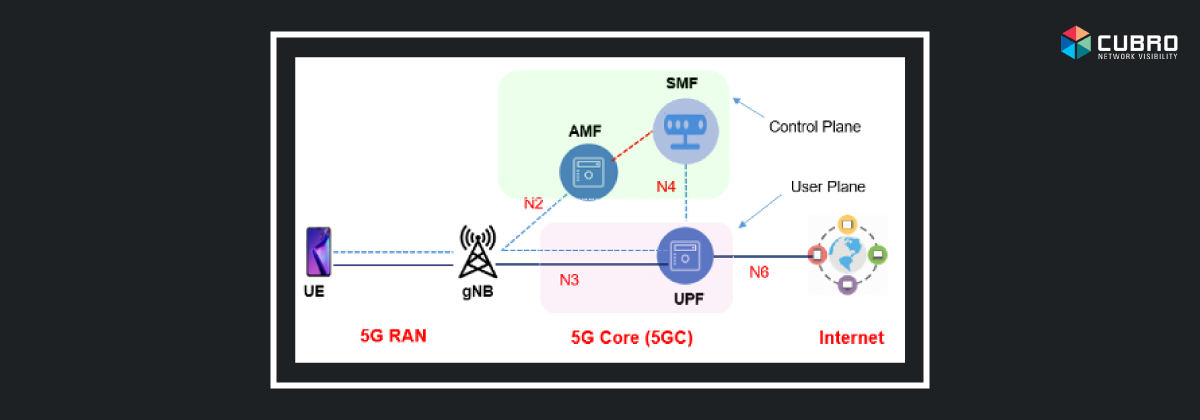
The importance of the 5G SA lies in the 5G promise of fully supporting enhanced mobile broadband (eMBB), ultra-reliable low-latency communications (URLLC) and massive IoT use cases.
Cubro Visibility products, together with Cubro security solution partners, can play a critical role in protecting enterprise computing access by continually monitoring network activity on the network to identify and remediate these new threats.
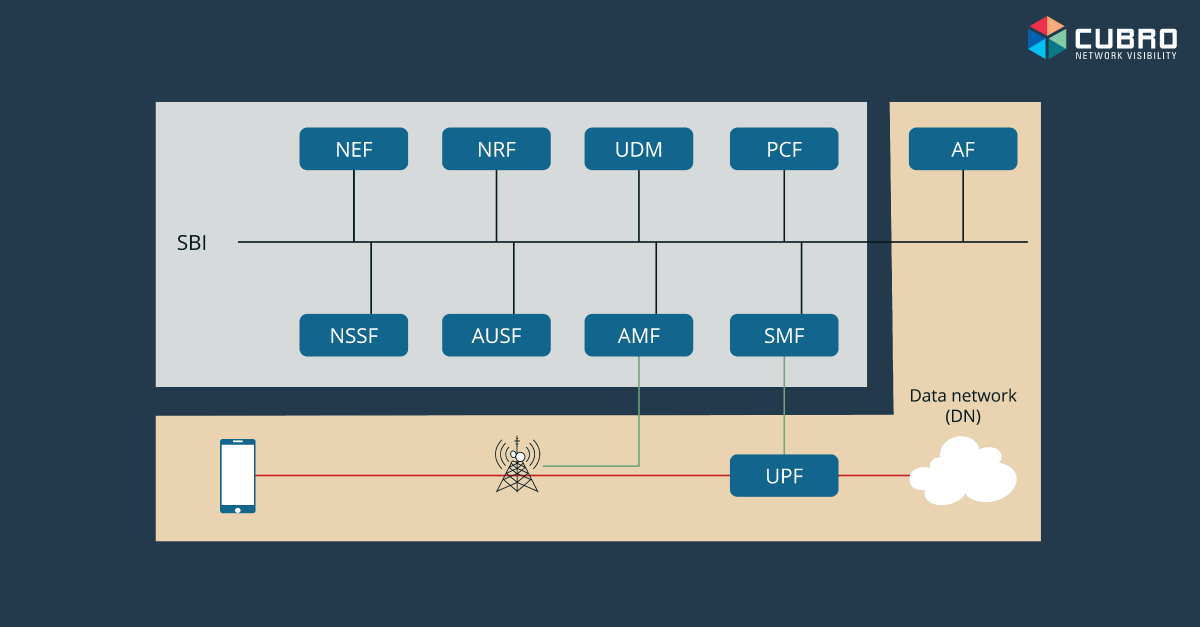
The Service Based architecture for 5G systems represents a move towards a cloud implementation of the Core Network. Newer 5G Core Networks have been deployed using virtualised Network Elements to allow multiple Network Elements to operate using a shared underlying hardware platform.