OT Security
Enhancing OT Security with Network Visibility Solutions
OT Networks
Why Visibility Matters in OT Networks
In today’s industrial environments, Operational Technology (OT) networks are no longer isolated systems. Once protected by an air gap (a network security measure employed on one or more computers to ensure that a secure computer network is physically isolated from unsecured networks) and physical separation, OT systems now connect with IT networks to support real-time monitoring, predictive maintenance, and centralised data analysis. This IT/OT convergence, while beneficial for efficiency, opens the door to new cybersecurity threats.
What is Operational Technology (OT)?
NIST defines OT as comprising a broad range of programmable systems and devices that interact with the physical environment. These systems and devices detect or cause a direct change by monitoring and/or controlling devices, processes, and events. Examples include industrial control systems (ICS), building automation systems, transportation systems, physical access control systems, physical environment monitoring systems, and physical environment measurement systems.

The primary difference between OT and IoT lies in their scope and focus. While IoT collects and exchanges data, OT focuses on monitoring and controlling physical processes and equipment. From a security perspective, IoT security focuses on protecting connected devices and their data, while OT ensures the availability and safety of the systems and processes.
Some of these OT characteristics include significant risks to the health and safety of human lives, serious damage to the environment, and severe financial issues, such as production losses, negative impacts on the nation’s economy, and the compromise of proprietary information.
OT has unique performance and reliability requirements and often uses OSs and applications that may be considered unconventional by typical IT personnel. Furthermore, the goals of safety and efficiency sometimes conflict with security in the design and operation of OT systems.
Operational Technology development
Initially, OT systems were isolated, ran proprietary control protocols, and used specialised hardware and software. Over time, OT systems have adopted IT practices to enable corporate business systems connectivity and remote access capabilities and are designed and implemented using industry-standard computers, operating systems (OSs), and network protocols. This has made them resemble IT systems with obvious benefits, but has also brought new challenges.
OT systems are now less isolated from the outside world than their predecessors, creating a greater need to secure OT systems. Point-to-point serial cables are increasingly changed to wireless solutions, thus creating a higher risk from adversaries who don’t need any more physical access to the cables. While security solutions have been designed to deal with these issues in typical IT systems, special precautions must be taken when introducing these same solutions to OT environments. In some cases, new tailored security solutions are needed.
OT Devices and Industrial Control Systems (ICS)
Legacy OT devices and industrial control systems (ICS) have not been designed to face modern cyber threats. As these systems become more connected, often without robust security protocols, they become attractive targets for ransomware, unauthorised access, and advanced persistent threats (APT). What was once considered a secure, standalone network is now a critical part of an organisation’s larger and more vulnerable digital ecosystem.
Some OT protocols are 45 years old, and they were designed for serial interfaces to be used in SCADA systems. There are a plethora of protocols used today, Modbus, DNP(3), IEC 61850 and Siemens S7, to mention a few. Today, the protocols can be encapsulated with TCP/IP or UDP. This enables the use of more flexible packet routing and also makes it possible to share packets with various destinations using TAP and NPB. Wireshark can also be used to analyse the protocols. Below you can find a screenshot of Wireshark. The data is from https://www.netresec.com/?page=PCAP4SICS using https://cs3sthlm.se/
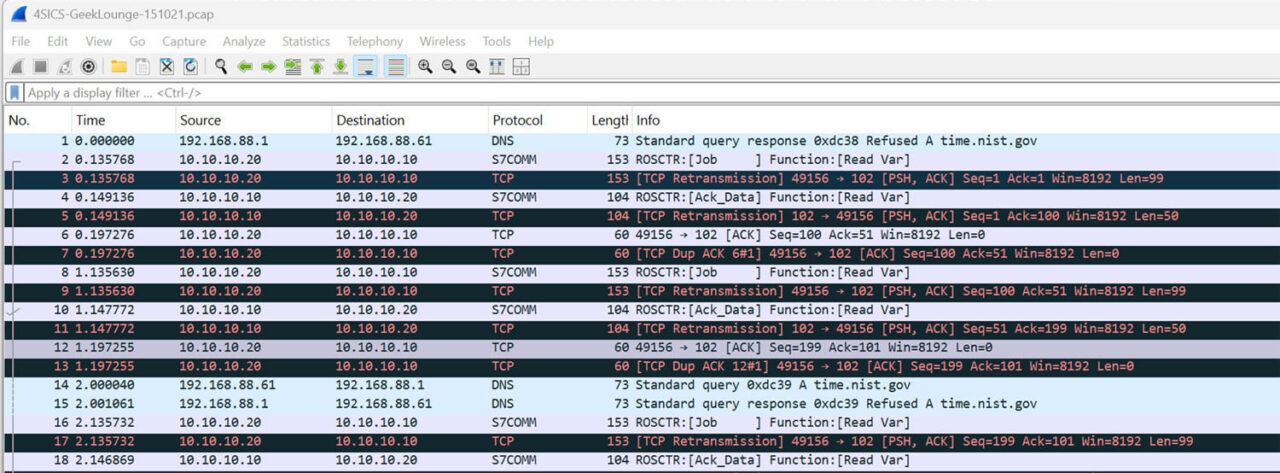
This screenshot shows Wireshark’s ability to open S7comm protocol from Siemens. It also practically demonstrates that TCP/IP-based or encapsulated protocols can be accompanied by DNS queries, showing the added security aspects to be aware of.
Purdue Model
Although the air-gap is no more a part of OT, it has had its comeback. The Purdue Model was designed as a reference model for data flows in computer-integrated manufacturing (CIM). This model later came to define the standard for building an ICS network architecture that supports OT security by separating the layers of the network. This separation allows for the maintenance of a hierarchical flow of the data between said layers. It illustrates the implementation of an air-gap between ICS/OT systems and IT systems.
The Purdue model has five levels. Field devices such as sensors and actuators are on the lowest level, 0. Level 1 includes local controllers, such as Programmable Logic Controllers (PLC). In recent times, levels 0 and 1 are combined. Level 2 introduces local supervision with alarm servers, historians and the control room. Site-wide supervisory is on the level 3 with management servers and with similar equipment as on level 2, but at the site level. Purdue model recommends DMZ for IT/OT boundary before entering level 4 with business systems. Level 5 is the enterprise network layer with Active Directory, Internal email, CRM and Security Operations Centre.
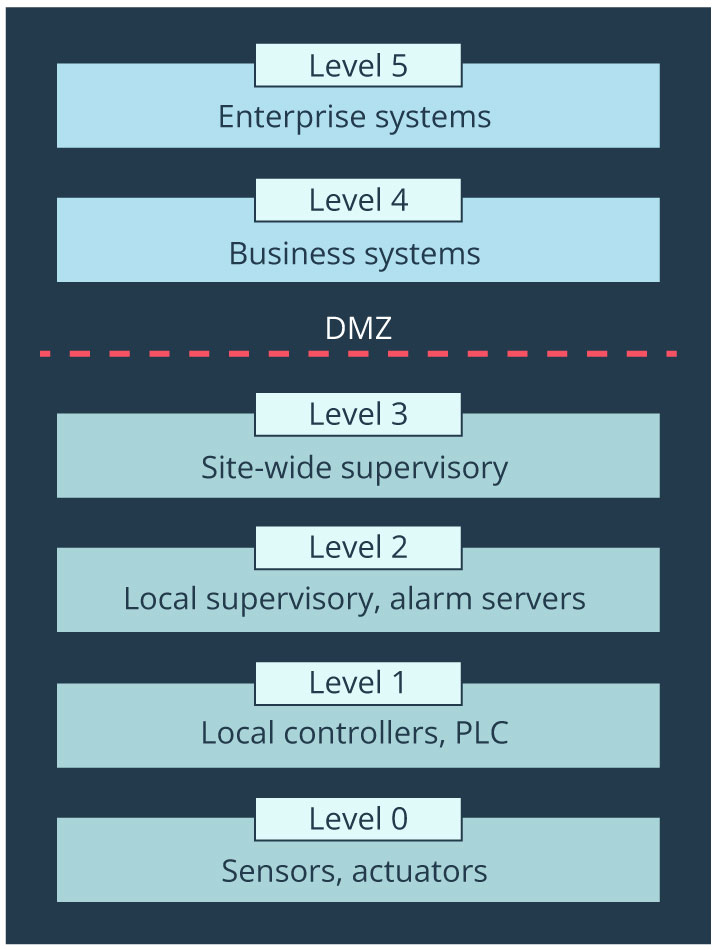
The Purdue model was never intended to be a cybersecurity reference model. It was created to depict best practices for managing the segmentation between the enterprise and industrial segments. Nevertheless, it has remained prevalent as a conceptual framework in IT/OT security adopted by many security vendors.
NIST recommendation for OT
Based on NIST recommendations, primary security objectives for an OT implementation should include the following:
- Restrict logical access to the OT network, network activity, and systems.
- Restrict physical access to the OT network and devices.
- Protect individual OT components from exploitation.
- Restrict unauthorised modification of data.
- Maintain functionality during adverse conditions.
- Restore and recover the system after an incident.
A prerequisite for OT security is the inventory of the assets in the network. Inventory can be performed using either passive discovery or active polling. Passive discovery requires a longer time to detect the devices, but its interaction with the network is smaller. Typically, the data is collected using port spanning with the existing switches. If there are no existing switches, installation of either a TAP or a switch is needed. This creates a challenge, as in most cases, the maintenance window for OT occurs only once a year. If the installation isn’t successful, the network can go down, causing significant losses.
Another approach is to poll devices actively. This method provides more details about the devices, but can cause problems if the polling messages are not formulated exactly correctly.
Several security companies are proponents of network segmentation and traffic analytics for threats and vulnerabilities. Similar to IT security, user identity and access management are essential components for security. The protection needs to be extended to both wired and wireless access.
OT Network Monitoring
When OT networks implement packetised transport, it is essential to have visibility into the traffic. Organisations must be able to monitor every packet, every port, and every protocol across their industrial infrastructure. Visibility enables security teams to:
Cubro’s network TAPs and packet brokers provide unfiltered, lossless access to all traffic, eliminating blind spots and enabling deep traffic inspection, without disrupting operations.
Benefits of a Dedicated OT Network Visibility Infrastructure
Complete Visibility & Elimination of Blind Spots
Cubro TAP (Test Access Point) devices offer 100% hardware-based visibility into OT network traffic, delivering complete, unfiltered access without dropping a single packet. Unlike software-based SPAN or switch port mirroring, which often results in packet loss, jitter, or incomplete data capture, Cubro TAPs operate passively and reliably at the physical layer, ensuring no interference with live operations.
This true line-rate visibility is essential for uncovering hidden threats and abnormal behaviour in OT environments. From PLC communication anomalies to unauthorised device access, you can’t detect what you can’t see, and Cubro ensures you see it all.
Seamless Integration with Security & Monitoring Tools
Cubro’s Network Packet Brokers (NPBs) act as intelligent traffic managers, aggregating data from multiple TAPs, filtering relevant traffic, and forwarding it to security and monitoring platforms. This ensures your IDS, SIEM, SOC, and analytics tools receive exactly the data they need – nothing more, nothing less.
By optimising traffic flow, Cubro NPBs help prevent tool overload, preserve the performance of security systems, and maximise ROI on your existing monitoring infrastructure. Whether it’s an intrusion detection system or a real-time monitoring dashboard, Cubro’s platform fits seamlessly into any industrial cybersecurity architecture.

Real-Time Monitoring for Proactive Threat Detection
In OT environments, where uptime and safety are critical, every second counts. Cubro enables real-time monitoring by capturing live traffic directly from the network. This empowers security teams to detect anomalies, policy violations, or suspicious behaviour as it happens, not after the damage is done.
OT systems vary a lot depending on the industry and purpose of the system. It would be tempting to offer TAP and network packet broker to standardise the collection, filtering and redistribution of the packets, but it may not always be the optimal solution. Old OT networks may be better left alone and protected with network segmentation. With new OT networks, it is highly recommended to design the security into the solution from the beginning including TAP and NPB.
How Cubro’s Solution Strengthens OT Security

As industrial networks continue their digital transformation, protecting Operational Technology (OT) environments from emerging threats becomes a top priority. The convergence of IT and OT networks increases exposure to cyber risks, making it critical to implement a dedicated, high-performance network visibility layer. Cubro provides a robust and scalable approach to OT visibility that significantly enhances cybersecurity posture across industrial systems.
In contrast to traditional methods like switch port mirroring, often prone to packet loss and limited insight, Cubro’s hardware-based TAPs (Test Access Points) deliver full visibility into network traffic without disrupting operations. These devices passively capture every bit and byte, ensuring a lossless and faithful copy of all data flows.
By eliminating visibility gaps and delivering unfiltered access to traffic from critical infrastructure, Cubro empowers OT teams to identify anomalies, policy violations, and potential threats before they impact operations.
Optimised Integration with Cybersecurity Infrastructure
To ensure security tools operate at peak efficiency, Cubro’s Network Packet Brokers act as intelligent intermediaries – aggregating, filtering, and distributing traffic to monitoring platforms such as Intrusion Detection Systems (IDS), Security Information and Event Management (SIEM) platforms, and Security Operations Centres (SOC).
This means you can maximise the value of your existing cybersecurity investments, avoid oversaturating tools with irrelevant data, and tailor traffic delivery for improved detection accuracy—all while maintaining the performance of mission-critical OT systems.
Tailored Solutions for Base-T (Copper) OT Networks
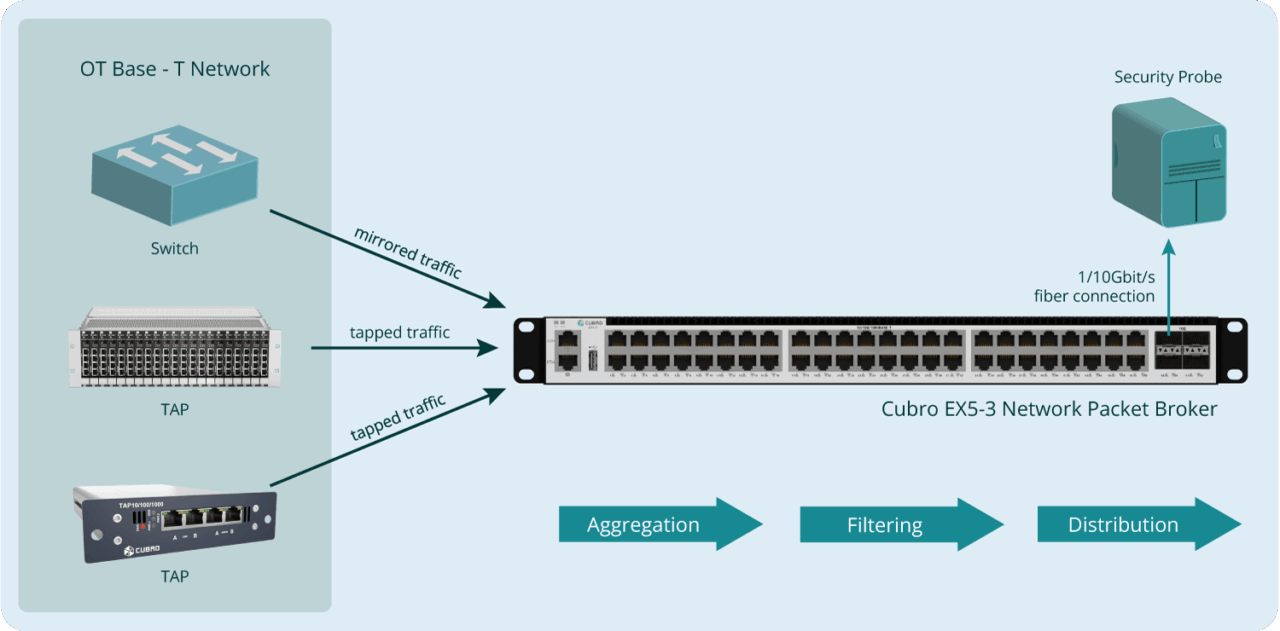
Many industrial environments still operate on copper-based infrastructure. Cubro delivers fit-for-purpose solutions that bridge legacy systems with modern security demands:
FlexTAP Copper Chassis Solutions
EX5-3 Network Packet Broker
OT Security with Cubro
With over two decades of experience in network visibility, Cubro delivers proven solutions that enhance OT security, reduce operational risk, and provide the transparency needed to protect critical infrastructure.
Cubro’s solution benefits:
Selecting the right network visibility infrastructure for OT environments is critical. OT systems prioritise availability and safety, and visibility solutions must respect these operational requirements while enhancing security and observability.
Contact Us for a Consultation

Our newsletter provides thought leadership content about the industry. It is concise and has interesting content to keep you updated with what’s new at Cubro and in the industry. You can unsubscribe anytime with a single click.
Your e-mail address is only used to send you our newsletter and information about the activities of Cubro Network Visibility. You can always use the unsubscribe link included in the newsletter.



