Your Cybersecurity Strategy Starts Here

Why network visibility matters for cybersecurity?
Higher ROI – A single investment in Cubro can reduce long-term cybersecurity expenses by cutting licensing, bandwidth, and maintenance costs.
Better Security Outcomes – Security tools perform better when they receive only relevant traffic, improving overall threat detection and response.
More Strategic IT Investments – Instead of overspending on bigger security tool licenses, companies can allocate budgets more effectively.
How Network Visibility Empowers Enterprise Security
Since enterprises have started to use the cloud more extensively, the network environments have become more challenging to monitor and protect. Traditional tools often struggle to keep up with this scale and complexity, leading to inconsistent visibility and potential blind spots.
What is Cybersecurity Monitoring?
Cybersecurity monitoring is the automated process of collecting and analyzing indicators of potential security threats and triaging them with appropriate action.
Security operations teams have an ever-increasing amount of work and responsibility in maintaining the overall health, performance, and security of a business’ infrastructure as technologies evolve, complexity increases, and enterprise networks continue to grow.
The High Cost of Data Breaches
Today cybersecurity monitoring is part of a company’s compliance and regulatory requirements. Data breaches can be costly in many ways: ransom cost, fines and compensations, bad publicity, lower brand value and paused operations preventing business activities. Some of these can have a long-lasting impact on the company, including lowered stock value.
Network cybersecurity monitoring’s core objective is to minimise downtime by preventing attacks and preserving data to keep an organization operational. By combining attack and passive security monitoring and automating the processes as much as possible, organizations can protect themselves from network threats and identify attackers.
Common Cybersecurity Pain Points in Large Enterprises
Several tools are on the market for security departments or security operations centres (SOC). SOC is the team and infrastructure responsible for managing an organization’s security posture, leveraging tools like SIEM and SOAR. Security information and event management (SIEM) collects and analyzes security data, identifying potential threats. Security orchestration, automation and response (SOAR) automates and orchestrates responses to security incidents, improving SOC efficiency.
Network detection and response (NDR) refers to a category of network security products that detect abnormal system behaviours by continuously analyzing network traffic. Endpoint Detection and Response (EDR) is used for unusual activity on system endpoints, including computers, phones, and servers.
Together, network and security monitoring provide comprehensive information, analysis, and reports. The aim is to automate these functions as much as possible.
Automation tools and particularly agentic AI help in making these tasks easier.
Finding the Right Balance
On the one hand, it is tempting to choose the best of breed tools to create a best of industry service operation centre, but integrating
them always comes with a cost. On the other hand, one vendor solution minimises the integration costs, but the risk of vendor lock-in is not appealing. Often, one vendor solution is criticised for its limited agility. Network Packet Brokers increase flexibility by providing the option of sending the same or filtered traffic to several destinations. This enables using tools in parallel, for example, when testing and comparing tools to each other or when having tools for specific purposes.
Regardless of what kind of solution is chosen, cost monitoring is essential. The cost overruns are due to licensing, bandwidth charges, and inefficient use of tools. The number of servers often has an impact on the licensing fees and sometimes upgrading the HW and reducing the number of servers can create substantial savings. Bandwidth and efficient use of the tools can be favorably improved by using TAP and NPB solutions.
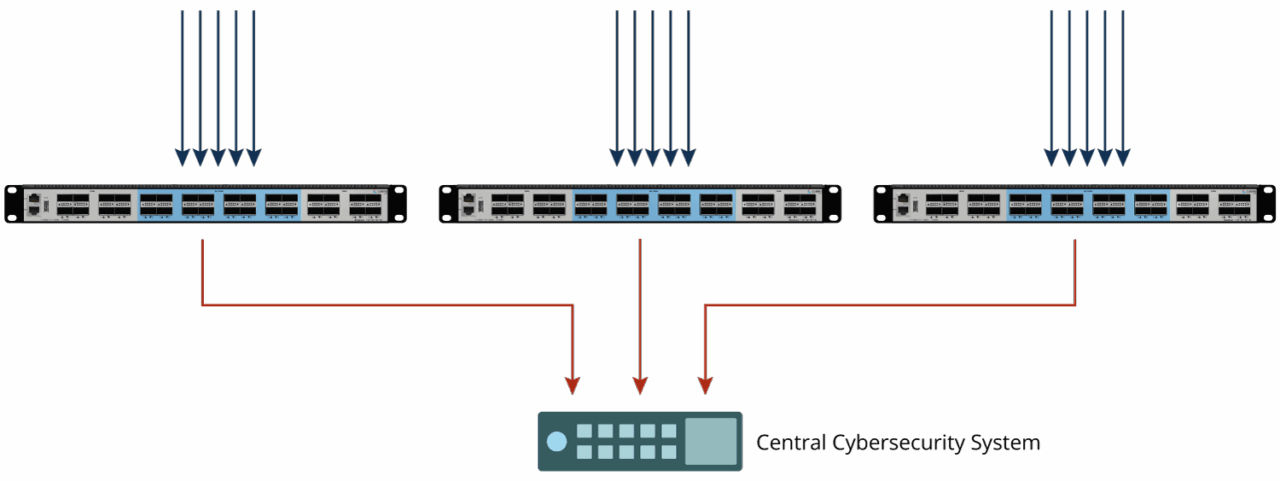
Another area where TAP and NPB are helping is traffic reduction and filtering to choose only relevant traffic to remove performance bottlenecks. Security tools may require continuous HW and licence upgrades with increasing traffic.
In either case, it is important to have all necessary data for the tools.

Our newsletter provides thought leadership content about the industry. It is concise and has interesting content to keep you updated with what’s new at Cubro and in the industry. You can unsubscribe anytime with a single click.
Your e-mail address is only used to send you our newsletter and information about the activities of Cubro Network Visibility. You can always use the unsubscribe link included in the newsletter.



